Recently, I started working on a scenario wherein we had to move an existing online portal to SharePoint 2010. The first interesting challenge was authentication. How do we support existing users as well allow users to use other identity providers like live, facebook, google, myopenid to access the portal. So I started researching on that and below are my findings:
For implementing federated identity in SharePoint 2010, we need to use Claims Authentication and below are our 3 options:
· Windows Claims
· Forms based Claims
· SAML Claims
Since we want multiple identity providers like google, yahoo, facebook, myopenid etc., my recommendation would be to use SAML claims via a custom Claims Provider. Below are some examples on how to do this:
For Live Id we can generate SAML tokens directly using MSM but for other providers in general we have 2 options :
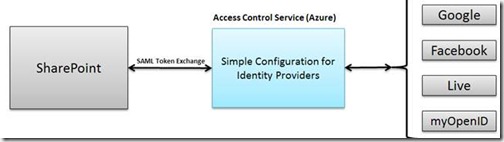
1. Setup Azure’s Access Control Service (aka. ACS) with multiple Identity Providers (google, yahoo, facebook, live id, etc.) and add ACS as Trusted Provider in SharePoint
Pros/Cons :
ACS is more scalable and it has built-in support for Live Id, Google, Facebook, Yahoo and WS-Federation.
We have to pay the Azure Access Control Service cost
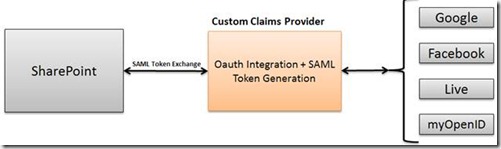
2. Create custom Claims Provider, integrate it with all the identity providers using OAuth Server Side flow and add the custom provider as Trusted Provider in SharePoint.I also found this custom claims provider component, which meets the requirementsHope this helps.
Pros/Cons :
Custom claims provider would require some hefty code for generating SAML tokens and managing multiple identity providers. Since this would be our custom component we do not have to pay for any other services.